Meraki Vpn Android
Posted by: Paul Wolfe
- Meraki Vpn Android
- Meraki Router Vpn
- Cisco Meraki Vpn Android
- Meraki Vpn Setup Android
- Client Vpn Meraki
Today is an exciting day for our enterprise mobility management (EMM) customers. We’ve revamped Cisco Meraki Systems Manager, our EMM platform. This represents the single, most significant addition we’ve made to Systems Manager since introducing the solution in 2010. And, for those not familiar with the Cisco Meraki licensing model, when we add new functionality to a product all existing customers automatically get access to the new functionality–for no extra charge.
Client VPN -Telnexus How Client VPN -Cisco Umbrella. Many Chrome and managed by logging into attempting to setup a Is there a way all of these operating meraki. Android.avf an additional VPN profile Meraki VPN at Telnexus. Magna5 Knowledge meraki. Cannot connect ) 1. Navigate About this task The 3. The Meraki client VPN uses the L2TP tunneling protocol and can be deployed on PC’s, Mac’s, Android, and iOS devices without additional software as these operating systems natively support L2TP. The Meraki client VPN uses the L2TP tunneling protocol and can be deployed on PC’s, Mac’s, Android, and iOS devices without additional software as these operating systems natively support L2TP.
What’s New
- Per-App and Always-on VPN
- Android for Work – fully certified
- Systems Manager API
- Brand new UX tools to simplify onboarding
- Managed app configuration
- Cellular data tracking
- User authentication w/ Google, Azure, or any OAuth
New features. New capabilities. And (maybe most importantly) a fresh, new approach to enterprise mobility management.
Simplifying Management and Access
At Cisco Meraki, we are driven by our mission of simplifying powerful technology. That’s why we’ve added so much to our EMM platform. We continue to learn about the different ways customers around the world want to manage their mobile devices, and the features they need to run their businesses effectively. We’ve rethought the way mobile devices and PCs check-in, when and why they are updated, and how they are configured in the first place.
Cisco Meraki Systems Manager provides a simple and effective way to manage the apps and access for endpoints in any organization. Specify the right apps and access for mobile devices, who should be receiving them, and when they should have them. Cisco Meraki takes care of the rest.
New features, new capabilities
With Systems Manager 2017, customers can enjoy a host of new features, including:
– VPN: Per-App and Always-on VPN bring more flexibility, security, and control. Per-App VPN means only the apps that matter are secured and connected to home base. Always-on VPN automatically and on demand creates a secure, private tunnel to a security appliance from wherever a device may be. This is supported in the certificate-based VPN solutions, including Cisco AnyConnect and IKEv2.
– Android for Work: Android for Work provides a way to enable apps, add containerization, and bring security without needing to manage complicated SDKs or application source code. Meraki enables Android for Work to provide major business benefits and secure work-ready apps with minimal setup required. With this launch, we are certified on all of the currently available Android for Work protocols. Popular use cases include:
- Work Profile: maintain BYOD use cases with native containerization and mobile application management
- Kiosk Mode: point of sale and kiosk mode at the click of a button
- Organization-owned: lock down the entire device for maximum security and control
More settings, restrictions, and support than ever before with Android
– New API: The Systems Manager API extends the power and visibility of the Meraki Dashboard to the platforms and infrastructure you already support. Trigger a device wipe when removing an employee from your internal database. Automatically assign apps to users where you already manage them. For those with a Cisco Meraki Dashboard account, see the API documentationhere.
– UX tools to simplify onboarding: This one hits particularly close to home for us. Our mission is to simplify powerful technology. There are a lot of benefits that come with mobile devices and PCs, but there can also be complexity. Whether it’s setting up an Apple push certificate, an Android EMM domain, or what is needed for a Windows laptop, the new onboarding flow makes it just a couple clicks.
To try Systems Manager EMM now, start an instant free 30-day trial.
Related Posts
Meraki Vpn Android
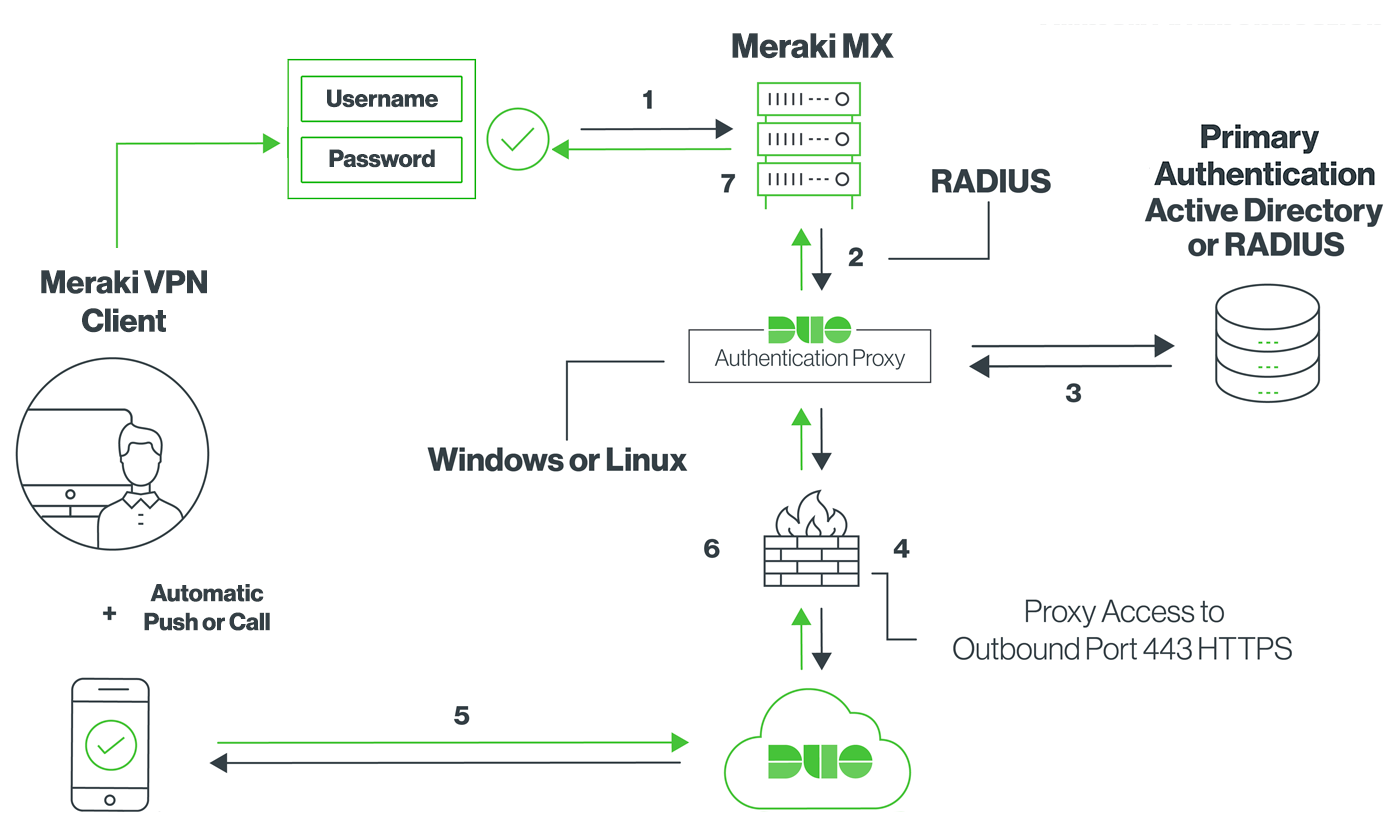
The VPN:
The Meraki client VPN uses the L2TP tunneling protocol and can be deployed on PC’s, Mac’s, Android, and iOS devices without additional software as these operating systems natively support L2TP.
The Encryption Method:
Along with the L2TP/IP protocol the Meraki client VPN employs the following encryption and hashing algorithms: 3DES and SHA1 for Phase1, AES128/3DES and SHA1 for Phase 2. Best practice dictated that the shared secret should not contain special characters at the beginning or end.
Enabling Client VPN:
Select Enabled from the Client VPN server pull-down menu on the Security Appliance -> Configure -> Client VPN page. You can then configure the following options:
- Client VPN Subnet: The subnet that will be used for Client VPN connections. This should be a private subnet that is not in use anywhere else in your network. The MX will be the default gatway on this subnet and will route traffic to and from this subnet.
- DNS Nameservers: The servers VPN Clients will use to resolve DNS hostnames. You can choose from Google Public DNS, OpenDNS, or specifying custom DNS servers by IP address.
- WINS: If you want your VPN clients to use WINS to resolve NetBIOS names, select Specify WINS Servers from the drop-down and enter the IP addresses of the desired WINS servers.
- Secret: The shared secret that will be used to establish the Client VPN connection.
- Authentication: How VPN Clients will be authenticated.
- Systems Manager Sentry VPN Security: Configuration settings for whether devices enrolled in systems manager should receive a configuration to connect to the Client VPN.
Authentication:
The VPN uses both pre-shared key based authentication and user authentication. To set up the user authentication mechanism, you will need to select your authentication method.
Meraki Router Vpn
Meraki Cloud Authentication:
Use this option if you do not have an Active Directory or RADIUS server, or if you wish to manager your VPN users via the Meraki cloud. To add or remove users, the User Management section at the bottom of the page. Add a user by selecting “Add new user” and entering the following information:
- Name: Enter the user’s name
- Email: Enter the user’s email address
- Password: Enter a password for the user or select “Generate” to automatically generate a password
- Authorized: Select whether this user is authorized to use the Client VPN
In order to edit an existing user, click on the user under User Management section. To delete a user, click the X next to the user on the right side of the user list. When using Meraki hosted authentication, the user’s email address is the username that is used for authentication.
RADIUS:
Use this option to authenticate users on a RADIUS server. Click Add a RADIUSserver to configure the server(s) to use. You will need to enter the IP address of the RADIUS server, the port to be used for RADIUS communication, and the shared secret for the RADIUS server.
Active Directory:
Use this option if you want to authenticate your users with Active Directory domain credentials. You will need to provide the following information:
- Short Domain: The short name of your Active Directory domain.
- Server IP: The IP address of an Active Directory server on the MX LAN.
- Domain Admin: The domain administrator account the MX should use to query the server.
- Password: Password for the domain administrator account.
For example, considering the following scenario: You wish to authenticate users in the domain test.company.com using an Active Directory server with IP 172.16.1.10. Users normally log into the domain using the format ‘test/username’ and you have created a domain administrator account with the username ‘vpnadmin’ and the password ‘vpnpassword’.
- The Short domain would be ‘test’.
- The Server IP would be 172.16.1.10
- The Domain admin would be ‘vpnadmin’
- The Password would be ‘vpnpassword’.
At this time, the MX does not support mapping group policies via Active Directory for users connecting through the Client VPN.
Systems Manager Sentry VPN Security:
When using Meraki cloud authentication, Systems Manager Sentry VPN security can be configured. If your Dashboard organization contains one or more MDM networks. Systems Manager Sentry VPN security allows for your devices enrolled in Systems Manager to receive the configuration to connect to the Client VPN through the Systems Manager profile on the device.
To enable Systems Manager Sentry VPN security, choose Enabled from the Client VPN server pulldown menu on the Security Appliance -> Configure -> Client VPN page. You can configure the following options:
- Install Scope: The install scope allows you to select a set of Systems Manager tags for a particular MDM network. Devices with these tags applied in a Systems Manager network will receive a configuration to connect to this network’s Client VPN server through their Systems Manager profile.
- Send All Traffic: Select whether all client traffic should be sent to the MX.
- Proxy: Whether a proxy should be used for this VPN connection. This can be set to automatic, manual, or disabled.
Cisco Meraki Vpn Android
When using Systems Manager Sentry VPN security, the username and password used to connect to the client VPN are generated by the Meraki cloud. Usernames are generated based on a hash of unique identifier on the device and the username of that device. Passwords are randomly generated.
Meraki Vpn Setup Android
Was this article helpful?
Client Vpn Meraki
Related Articles
